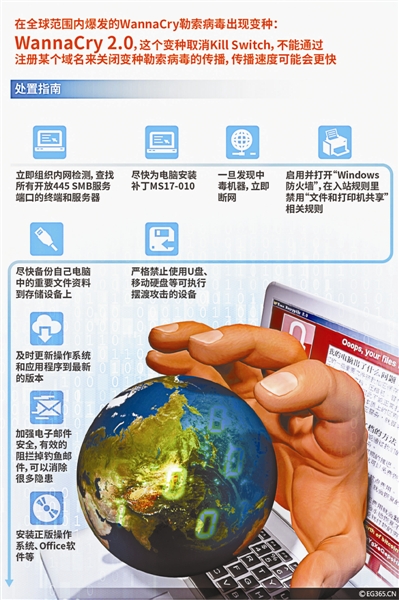
The impact of the WannaCry ransomware virus sweeping the world continues, and at least 150 countries are currently under cyber attacks. The reporter of Beijing Youth Daily learned that in addition to the network attacks on many colleges and universities in China, a considerable number of computers of enterprises and institutions were also recruited. According to British media reports, a 22-year-old British network engineer noticed that the blackmail virus had been constantly trying to enter an extremely special and non-existent website, he conveniently registered the domain name and unexpectedly blocked the spread of the virus. Unfortunately, the ransomware will continue to spread in the future. Yesterday afternoon, the national network and information security information notification center urgently reported that a variety of ransomware broke out worldwide, and the “anti-virus method” accidentally discovered by British guys had expired. Many domestic units have been attacked by viruses. On the evening of May 12, WannaCry ransomware spread in many countries around the world. The networks of many domestic universities were attacked by ransomware, and a large number of important materials such as students’ graduation papers were encrypted by viruses, only the payment of ransom can be restored. Yesterday, the reporter of Beiqing Daily learned that not only campus network, but also some enterprises and institutions were affected by the virus. According to a staff member of Zhengzhou branch of China Unicom, on May 14, due to the influence of Bitcoin ransomware, all the computers of the unit were paralyzed. On May 13, the Exit-Entry office of Xiangshui public security bureau released a message saying that the exit-entry business was temporarily suspended due to a new virus attack on the public security network, and the specific recovery time was waiting for notice. “After a whole night, the data has not been recovered.” Yesterday, a policeman in Shandong told the reporter of Beiqing Daily that the computer that stores data in the unit was locked due to the blackmail virus, and he could only do nothing to learn computer major. Some gas stations of PetroChina are affected Also affected are PetroChina gas stations. Yesterday, PetroChina announced on its official website that around 22:30 on May 12, due to the outbreak of the global bitcoin ransomware virus, the normal operation of some gas stations belonging to the company was affected. The virus makes online payment functions such as gas station fuel card, bank card, and third-party payment unavailable. However, basic businesses such as refueling and sales are operating normally, and the security of fuel card account funds will not be affected. Yesterday afternoon, the reporter of Beiqing Daily got in touch with five PetroChina gas stations in Beijing. Among them, the staff of No. 12 gas station of China National Petroleum Corporation said that since the 13th, due to the impact of the new virus, various payment methods such as mobile phone payment and fuel card payment at the gas station have been affected, although emergency repair was carried out in the morning, the network was still unstable. The staff of China National Petroleum gas station told the reporter of Beiqing Daily that as of 4 pm, the national gas station still only accepted cash payment or fuel card of the national gas station. PetroChina said yesterday afternoon that it began to carry out the restoration work station by station according to the technical solutions verified on site. More than 80% of gas stations have recovered their network connections, and infected gas stations are gradually recovering fuel card, bank cards, and third-party payment functions. The staff of PetroChina Dahu Villa southwest, PetroChina EASTROC gas station and PetroChina Jingshun gas station told the reporter of Beiqing Daily that the functions of mobile phone payment and fuel card payment had been restored before noon. The spread of the virus was once accidentally blocked. News from Britain seems to bring a glimmer of hope to defeat the ransomware. British media reported on the 13th that a 22-year-old British network engineer noticed on the evening of the 12th that the ransomware was constantly trying to enter an extremely special and unexistent website, so he conveniently spent 8.5 pounds (about 75 yuan) to register the domain name, trying to use this website to obtain relevant data of ransomware. Surprisingly, the further spread of ransomware around the world has been blocked since then. This engineer and colleague analyzed that this strange website is probably a “checkpoint” set by ransomware developers to avoid being captured by cyber security personnel “, however, the behavior of registering the website unintentionally triggered the” suicide switch “provided by the program”. In other words, the ransomware must visit this non-existent website before each attack. If the website continues to exist, it means that the ransomware has not attracted the attention of security personnel and can continue to travel freely on the Internet; once the url exists, it means that the virus may be intercepted and analyzed. In this case, in order to avoid being controlled by network security personnel to obtain more data or even in turn, the ransomware will stop spreading. New variants of ransomware have emerged British network engineers and some network security experts who accidentally blocked the ransomware said that this method only temporarily prevented the further attack and spread of the ransomware, however, it cannot help those users who have attacked the ransomware, nor does it completely crack the ransomware. They speculate that the new version of ransomware is likely to make a comeback without this “suicide switch. This speculation really soon became a reality. Yesterday, the national network and information security information notification center urgently reported: monitoring found that the WannaCry Blackmail virus that broke out worldwide had a variant: WannaCry 2.0, which was different from the previous version, this variant cannot disable the spread of a variant ransomware by registering a domain name, which may spread faster. The Beijing Municipal Party Committee network information office, the Beijing Municipal Public Security Bureau, and the Beijing Municipal Economic and Information Commission also jointly issued the Notice on suggestions on the emergence and disposal of WannaCry ransomware worms. This notice requires all units to immediately organize internal network detection. Once a poisoned machine is found, the network will be disconnected immediately. It is strictly prohibited to use devices that can perform ferry attacks such as USB disks and mobile hard disks. According to the notice, it seems that formatting the hard disk can remove viruses. The European Cyber Crime Center, affiliated to the European Union Criminal Police Organization, said on the 13th that the scale of the ransomware attack was unprecedented and it was necessary to find suspects through complex international investigations, europol has cooperated with many countries to investigate the attack. Text/Our reporter Wang Tianqi integrated Xinhua news agency for pictures/Oriental IC The impact of the 2533 WannaCry ransomware virus sweeping the world continues, and at least 150 countries are currently under cyber attacks. The reporter of Beijing Youth Daily learned that in addition to many colleges and universities in China, there are also quite a number of enterprises and enterprises.