The inside story is amazing enough that the blackmail virus has not ended yet.
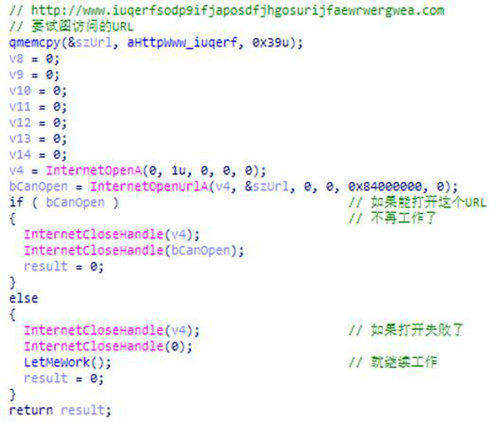
The outbreak of ransomware WannaCry (Eternal Blue) around the world is probably the most influential public security event these days. Since last Friday night, news of the outbreak of ransomware has spread among students from one of the Friends of chivalrous Island. At that time, the virus infection was mostly within the range of campus network. As the graduation season was approaching, many laboratories and students’ graduation designs and papers were severely affected. Over the past weekend, many friends of Uncle Dao were pulled back to the company or unit to work overtime and patch them to prevent large-scale infection caused by the “startup tide” on Monday workdays. In spite of this, today, in the news report, we still saw the news that many domestic universities, gas stations, railway stations, self-service terminals, hospitals, government-run terminals and so on were infected by this virus. Event I believe you have read many articles about the outbreak principle of the virus these days. In short, this worm ransomware attacks users by targeting a vulnerability in Windows, and implements high-intensity encryption of documents and pictures in the computer, and ask the user for the ransom paid in bitcoin. Otherwise, after seven days, the data cannot be recovered even if the ransom is paid. The encryption method is very complex, and each computer has different encryption serial numbers. With the current technical means, decryption is almost “helpless”. In today’s global network interconnection, the victims are certainly not limited to China. According to statistics from the 360 Threat Intelligence Center, after the outbreak on the 12th, more than 100000 organizations and institutions in nearly 100 countries around the world were captured, including 1600 American organizations and 11200 Russian organizations, more than 29000 IP addresses are infected in China. In Spain, the network systems of many companies including telecom giant Telefonica and power company Iberdrola, energy supplier Gas Natural were paralyzed; Portugal Telecom, American transportation giant FedEx, a local government in Sweden, russia’s second largest mobile telecom carrier Megafon have been exposed to attacks. According to Europol, the attack has affected 150 countries and regions. As the virus version is updated and iterated, the specific number may increase. Then, the question arises: Who did this?! Black Hand There is no answer. In the words of Zheng Wenbin, the head of 360 core security team, the traceability of ransomware has always been a difficult problem. The FBI once offered a reward of 3 million dollars to find the author of the ransomware, but there was no result. At present, there is no country in the world where the author of the ransomware comes from. However, from the perspective of blackmail, ransomware prompts in 15 languages including Chinese will appear after the computer is infected with the virus, and the whole payment will be carried out in such a very difficult way as Bitcoin and anonymous network, it is likely to be the organizational behavior under the Black industry chain. Ransomware is a new virus model that began to appear in 2013. Since 2016, the virus has entered the outbreak period. Up to now, more than 100 ransomware have benefited from this behavior. For example, last year, a variant of the CryptoWall virus family received 2.3 billion ransom. In recent years, different types of ransomware have also appeared in Apple computers, Android and iPhone phones. Although the underhand cannot be found at present, the tools it uses clearly point to an organization-NSA(National Security Agency), the US National Security Agency. This organization, also known as State secrets bureau, is affiliated to the U.S. Department of Defense and is the largest intelligence department among U.S. government agencies, specializing in collecting and analyzing foreign and domestic communication data. The eternal blue used by hackers is the network weapon developed by NSA against Microsoft MS17-010 vulnerabilities. Here’s the thing: the NSA itself has a large number of well-developed cyber weapons in its hands, but in June, 2013, more than a dozen weapons such as “Eternal Blue” were stolen by the hacker organization “Shadow Broker” (ShadowBreakers). In March this year, Microsoft released patches for this vulnerability, but first, some users did not have the habit of patching in time, second, many users around the world are still using earlier versions such as WindowsXP, which have stopped updating services, and cannot obtain patches, thus causing widespread spread around the world. With the feature of “worm” constantly scanning, it is easy to repeatedly infect the Internet and the intranet of campus, enterprise and government agencies. Another question came: Why Did NSA know Microsoft’s vulnerabilities and made special cyber weapons, and then some of these weapons fell into the hands of hackers? NSA Realistically speaking, as one of the operating systems, Windows is composed of hundreds of millions of lines of code. The logical relationship between them cannot be decided by one person, so it is difficult to eliminate vulnerabilities. Windows is the most commonly used operating system in the world, so it is normal for hackers to study vulnerabilities and attack them for profit. But as the National Security Agency of the United States, it is just to stare at the loopholes in this system, and it also specializes in weapons. What is the reason? In fact, Microsoft did not know the vulnerability existed until the hacker organization exposed it. In other words, only the NSA knows that the vulnerability exists, and only they know how long it has been known. In the opinion of cyber security experts on chivalrous island, it is very likely that NSA has known this vulnerability for a long time and exploited it, but this time it was used by the criminal team, that causes such great harm. From this point, we can see that the technology of the United States is really strong, and it is a unique global in the field of network security. At the same time, “vulnerability” has become a valuable strategic resource that soldiers must fight. In other words, attacking the reality through the network is no longer the scene patent of science fiction movies, but the reality that has happened. If you don’t believe me, tell you a true story– Snowden, the one who disclosed the “prism plan” that the US government monitored the world, was a former employee of the NSA. He confirmed that in 1999, the Obama administration ordered the use of cyber attack weapons-a virus codenamed “Zhenzhen network” to attack Iran’s nuclear facilities. The reason is complicated. In short, Israel managed to purchase centrifuge control software with a virus in Iran through Malaysian software companies. In 2010, the virus broke out, the centrifuges that controlled and destroyed Iran’s nuclear facilities, such as that, eventually caused permanent physical damage to more than 1,000 centrifuges and had to suspend the process of enriching uranium. This is also the first case of attacking and destroying the real world through virtual space in history, which has achieved the effect that only through military operations on the ground in the past. Last year, Ukraine’s power grid system was also attacked by hackers, resulting in power supply interruption for hundreds of households. How many cyber weapons does the NSA hold now? Of course, it is the secret of the United States. But according to WikiLeaks, not only does the NSA have it, but the CIA also has it, their network intelligence center has created more than 1,000 kinds of computer viruses and hacker systems-the number confirmed by Snowden in 2013. Therefore, after the outbreak of the “Eternal Blue”, the report of the New York Times said, “if it is confirmed that this incident was caused by cyber weapons leaked by the National Security Bureau (NSA), the government should be blamed because the U.S. government makes many hospitals, enterprises and other governments vulnerable to infection”. According to the NSA, its duty should be to “protect American citizens from attacks”; They have also accused many countries of carrying out cyber attacks on the United States. But the fact is just the opposite. The countries they blame are all victims of this virus. The cyber weapons they use to “defend” become the weapons used by hackers to attack American citizens. In the words of the national public broadcasting station, “This attack pointed out a fundamental problem in the security field, that is, the monitoring of the National Security Bureau is protecting the people or creating more irreversible damage, even exceeding its benefits”. Alert Of course, the NSA should reflect, although they have not yet come out to respond. But what is more worthy of reflection is an essential topic: Who is the master of network security? As far as this time, the decision-making process within the U.S. government is more worthy of criticism. There is a Process called VEP(Vulnerability Equity Process) inside, which is used to follow this Process when NSA or other U.S. government departments find a software Vulnerability, decide whether to expose the vulnerability. If the vulnerability is disclosed, Microsoft and other manufacturers can easily create patches, and the vulnerability disappears; If the vulnerability is not disclosed, these government departments can keep it for their own use for “law enforcement, intelligence collection or other aggressive use”. Although this process created by the Obama administration is neither a law nor a presidential decree, it has been implemented since 2008. In the eyes of people in other countries outside the United States, this process is obviously problematic: this process, which can almost be called “black box, the network security risks of the whole world are all determined by the internal mechanisms of the United States, and others are exposed to the risks without any doubt. In response, Microsoft President Brad Smith also said angrily on his blog, “If these government departments continue to hide in the dark and dig for loopholes in global computer systems, then make the so-called Arsenal to attack other countries or buy and sell, then you are the accomplices of cyber crime!” In this sense, Xi Jinping has said many times that “there is no national security without network security”, which is absolutely targeted. Just imagine, this virus is still within the controllable range. What if the next network attack is larger and the target is clearer? From the perspective of China, in most people’s impression, the last outbreak of the virus of this scale probably dates back to the “panda burning incense” more than a decade ago “. However, like this virus, it is rare to face the serious situation of “kidnapping” of important information once the trick is almost unsolvable. From the reaction of different places, the emphasis on network security is obviously different. The National Network Information Department, as well as Shanghai, Beijing and other provinces and cities, issued emergency notices almost on the 13th; The infection that occurred on the morning of the 15th was more in the central and western provinces. Some industry experts also pointed out that, for example, government, enterprises and institutions, campus and other institutions, many leaders still keep the concept of network security at the point of “Finding people to kill and kill viruses if computers are poisoned, many people also think that” physical isolation with intranet is fine “, and the concepts and protective measures are quite lagging behind. Things haven’t ended yet, and there are enough problems and shocks. This is like a public health event. It is the usual emphasis on safety and the degree of organization, which determines the extent to which the plague can spread. I have to say, this is a very vivid and profound network security education course. After all, today our personal information, assets, data, etc. have been increasingly connected with computers and networks, but this process is irreversible. The outbreak of the 5554 ransomware “WannaCry” (Eternal Blue) worldwide is probably the most influential public security event these days. Since last Friday night, the blackmail virus broke out in the student group of one of chivalrous island friends.